In our digital world, stories of password breaches and security mishaps are all too common, reminding us of the critical need for tight security. Consider these recent high-profile incidents:
- LinkedIn (2012): Over 100 million email and password combinations exposed.
- Ashley Madison (2015): Personal details of 32 million users leaked.
- eBay (2014): Attackers accessed 145 million users’ records through employee logins.
These incidents highlight the glaring need for robust security measures. AWS Cognito emerges as a powerful tool for managing user sign-up, sign-in, and access, ensuring smooth authentication processes across platforms.
What is AWS Cognito?
AWS Cognito, launched by Amazon in July 2014, streamlines the process of user sign-up, sign-in, and access management for both mobile and web applications. It efficiently manages authentication across different platforms, such as social networks and SAML/OpenID Connect, and grants temporary security credentials for accessing app backend resources on AWS or via Amazon API Gateway. Cognito simplifies the developer’s task by handling the complexities associated with user management and authentication systems.
Over time, AWS Cognito has established itself as a reliable option for developers, offering a robust set of features aimed at secure user management.
Competitors to AWS Cognito
While AWS Cognito is notable for its extensive features, it’s worth mentioning that there are alternatives that might offer specific features Cognito does not.
- Auth0: Popular for its customizable flexibility and easy-to-use interface.
- Okta: Known for strong security and extensive integration options.
- Firebase Authentication: Favored for its straightforward use and integration with Firebase services.
- Azure AD B2C: Chosen for seamless Microsoft ecosystem integration and its ability to scale with your business.
- Duende IdentityServer: Valued for granular authentication control and extensive customization options, though it now requires a subscription for bigger projects.
When exploring a user authentication and access management solution, consider each platform’s integration capabilities, scalability, upkeep expenses, security features, and cost to find the best fit for your application’s needs.
Common AWS Cognito Scenarios
AWS Cognito stands out as a versatile and secure solution for managing user identities and facilitating access to AWS services. With its two main components, user pools and identity pools, Cognito addresses a broad range of authentication and authorization needs. Let’s explore six common scenarios for AWS Cognito.
1. Authenticate with a User Pool
User pools serve as a comprehensive directory for your app users, offering sign-up and sign-in functionalities. Users can authenticate directly through the user pool or via third-party identity providers (IdPs) like Facebook, Google, and Amazon. This flexibility simplifies the authentication process, allowing direct access to AWS services or server-side resources.
2. Access Server-Side Resources with a User Pool
Following a successful sign-in, your application can leverage user pool tokens to control access to server-side resources. User pool groups further refine access control, enabling permissions management based on user roles. For developers, this means a streamlined approach to securing application resources.
3. Leverage API Gateway and Lambda with a User Pool
API Gateway integration empowers your users to access APIs securely, with user pool tokens validating their requests. This setup is ideal for applications requiring secure, scalable access to Lambda functions or custom APIs. Mapping user pool groups to IAM roles enhances permission management, ensuring a robust security model.
4. Access AWS Services with Both User and Identity Pools
After authenticating through a user pool, your app can exchange tokens for temporary AWS credentials via an identity pool. This scenario supports a seamless transition from authentication to accessing a wide array of AWS services, offering a cohesive and secure user experience.
5. Authenticate with Third-Party IdPs and Access AWS Services
Identity pools facilitate access to AWS services for users authenticated by third-party IdPs. By exchanging third-party tokens for AWS credentials, users gain a simplified path to accessing AWS resources, supporting both authenticated and guest user scenarios.
6. Access AWS AppSync Resources
AWS Cognito integrates seamlessly with AWS AppSync, allowing users to access GraphQL resources with ease. Whether leveraging user pool tokens for authorization or signing GraphQL requests with IAM credentials, Cognito ensures a secure and streamlined access strategy.
Why Consider AWS Cognito?
Choosing AWS Cognito brings several strategic advantages:
- Streamlined Operations: Cognito reduces the operational load by managing the infrastructure for user management, freeing your team to concentrate on core development.
- Scalability: With its managed service model, Cognito seamlessly scales to accommodate user growth, ensuring reliable performance.
- Security and Compliance: Benefit from AWS’s focus on security and adherence to international standards, ensuring your user data is handled securely.
- Cost-Effectiveness: Cognito’s pay-as-you-go model offers a cost-effective solution compared to self-hosted alternatives, especially when considering the broader costs associated with maintenance and scalability.
- Accelerated Development: Utilize Cognito’s SDKs and integrations for quick feature implementation, speeding up your development cycle.
- Global Reach: AWS Cognito’s worldwide availability ensures a responsive user experience across the globe.
- Comprehensive Management Tools: From user registration to account recovery, Cognito offers extensive tools for managing user identities across platforms.
For companies keen on minimizing dedicated resources for managing authentication and user management infrastructure, AWS Cognito offers an appealing solution. Its managed service nature eliminates the need for extensive in-house expertise or dedicated teams to handle security, scalability, and compliance. This aspect is particularly beneficial for businesses aiming to optimize operational efficiency and reduce overhead costs. By relying on Cognito’s robust and scalable infrastructure, businesses can allocate their valuable resources towards product development, customer engagement, and market expansion strategies.
AWS Cognito’s Offerings
AWS Cognito’s suite is designed to tackle the challenges of user identity management, providing:
User Sign-Up and Sign-In
Crafting your own sign-up and sign-in mechanism involves navigating through complex security measures, ensuring data protection compliance, and implementing encryption—all of which demand substantial resources and continuous upkeep.
AWS Cognito simplifies this process, offering a comprehensive authentication solution that covers everything from multi-factor authentication to social media integrations. This service allows you to focus on your application’s core features, saving time and resources while maintaining a high standard of security and user experience.
Choosing AWS Cognito for user sign-up and sign-in streamlines development, freeing you to dedicate more effort to what truly matters in your app.
Enhanced Security with MFA
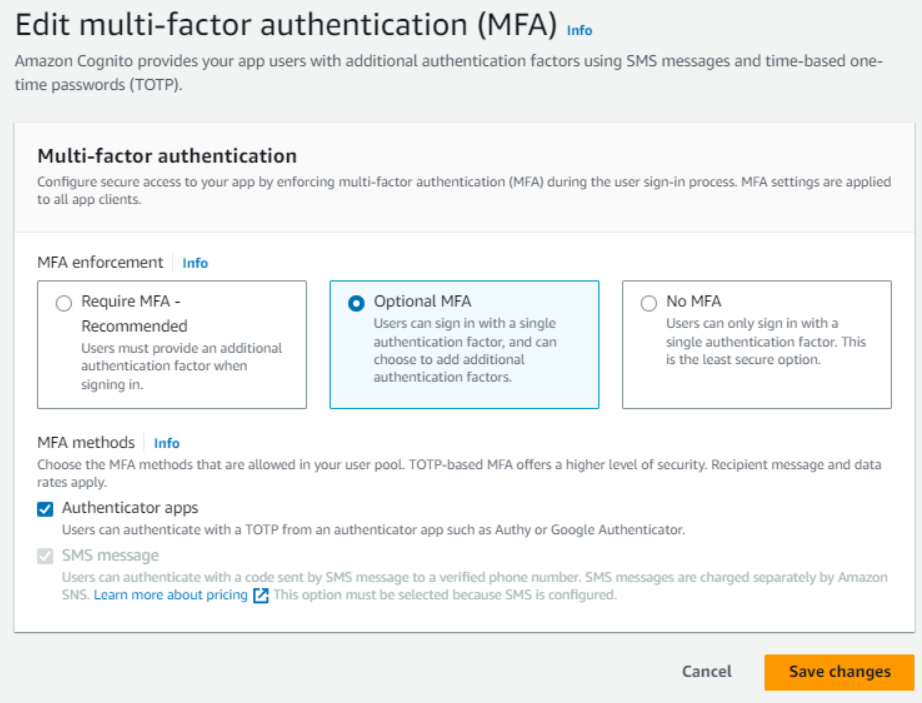
In today’s digital landscape, where password leaks are increasingly common, more companies are mandating Multi-Factor Authentication (MFA) to bolster security. AWS Cognito’s MFA introduces critical additional verification steps, significantly enhancing the safeguarding of sensitive user data. This reinforcement of security protocols ensures compliance with the strictest data protection standards, providing reassurance to both developers and users about the integrity of their information. By implementing MFA, AWS Cognito addresses the urgent need for more robust security measures in the wake of widespread password vulnerabilities, offering a reliable defence mechanism against potential breaches.
Customizable Authentication
AWS Cognito’s flexible architecture supports unique authentication workflows by integrating seamlessly with AWS Lambda, enabling you to create a customized sign-in experience that aligns with your application’s distinct characteristics. This integration opens up possibilities for advanced functionalities, such as fraud detection, by allowing you to embed custom logic into the authentication process. For instance, you could design a workflow that analyses sign-in attempts in real-time to identify and block suspicious activities, thereby enhancing the security of your application. This capability to interact with AWS Lambda not only enables personalized user experiences but also fortifies your app against potential threats, ensuring a secure and engaging environment for your users.
User Pool Management
Handling user profiles can often seem as challenging as organizing chaos, yet AWS Cognito’s User Pools simplify this task remarkably. They offer a scalable solution for efficiently organizing user information, making it easy to manage user profiles and sign-in credentials across different devices. With Cognito’s User Pools, maintaining control over user data becomes straightforward, reducing the complexity typically associated with such tasks.
Storing usernames and passwords—essentially, your users—outside your own database and instead with AWS Cognito can enhance your application’s security. By leveraging Cognito, you’re entrusting user credentials to a system designed with advanced security measures that adhere to stringent compliance standards. This not only minimizes the risk of data breaches but also offloads the responsibility of securing user data, including the implementation of encryption and the management of secure access protocols. AWS Cognito’s infrastructure is continuously updated to guard against the latest threats, providing an additional layer of security that can be more challenging to achieve with an in-house database. This approach not only safeguards your user information but also provides peace of mind, knowing that user data is handled by AWS’s robust security framework.
Direct Access Control
AWS Cognito’s Identity Pools do just that, providing secure, direct access to AWS resources. This direct access control mechanism eliminates the need for cumbersome credential management, ensuring a streamlined and secure user experience.
Considerations and Challenges with AWS Cognito
While AWS Cognito presents a powerful suite of features for managing user authentication and identity, like any technology, it comes with its own set of challenges and limitations. Understanding these potential drawbacks is crucial for developers and organizations to make an informed decision. Let’s delve into some of the disadvantages associated with AWS Cognito.
Flexibility vs. Complexity
Cognito offers customization options, from user pool management to integrating custom Lambda triggers for authentication workflows. However, this flexibility can also introduce complexity, especially for new users or small teams without dedicated AWS expertise. Navigating through the multitude of settings and options can be daunting, potentially leading to a steeper learning curve and longer setup times.
Customization Limitations
Despite its customizable nature, Cognito has its boundaries. Developers may find certain restrictions frustrating, such as limitations on the customization of the hosted UI or constraints on user pool attributes. These limitations might not align with all project requirements, compelling teams to seek additional solutions or workarounds to achieve their desired functionality.
Migration Challenges
Migrating to or from AWS Cognito can present challenges, particularly if there’s a need to transfer a large volume of user data. While Cognito supports data export, the process may not be as straightforward or comprehensive as required for complex migrations. This can lead to additional development work to ensure a smooth transition, affecting project timelines and resources.
Cost Considerations
While AWS Cognito operates on a pay-as-you-go pricing model, costs can escalate with increased usage, particularly for applications with a large number of users or those requiring advanced features like custom domain names for the hosted UI. It’s important for organizations to closely monitor their usage and optimize their Cognito setup to manage costs effectively.
Dependency on AWS Ecosystem
Using AWS Cognito ties your authentication and identity management closely to the AWS ecosystem. While this integration offers many benefits, it also increases dependency on AWS services. Organizations looking to maintain flexibility across cloud providers may find this dependency limiting, especially if there’s a future need to migrate services or diversify their cloud strategy.
Conclusion
AWS Cognito is a robust solution for handling user authentication and identity management, offering a wide range of features designed to secure and streamline user access. However, its complexities, customization limits, regional availability concerns, migration challenges, cost considerations, and dependency on the AWS ecosystem are factors that organizations need to consider. By weighing these disadvantages against the benefits, teams can make an informed choice that aligns with their project requirements, ensuring they leverage AWS Cognito’s strengths while mitigating its limitations.

